What Step Is Part of Reporting of Security Incidents
Step 2 Complete Security Incident Report. All it takes is acknowledging that youve received notice of the incident.
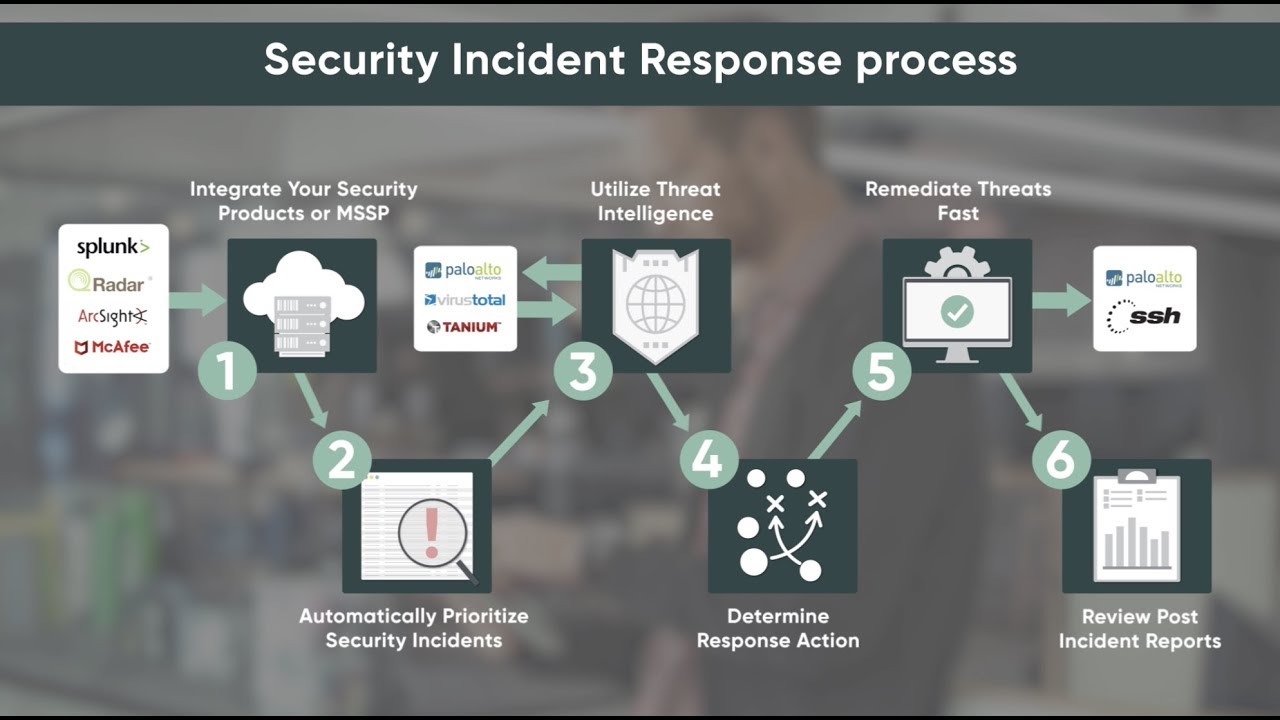
Understanding Security Incident Response
Security Incident Reporting Procedures Step 1 Report Crime to local law enforcement if required.

. The information security incident reporting form is an important first step in handling information security incidents in a coordinated response. In order to have an effective cyber security program you need eyes and ears everywhere. The ability to continue after a disaster of some kind is a requirement of Security Rule.
Its the first step really and its easy. Most contract security companies have a reporting system that is used by their security officers to report security incidents. Monitor security events in your environment using firewalls intrusion prevention systems and data loss prevention.
The Importance of Security Incident Reporting. The update to FISMA is an important first step toward solving supply chain security problems exposed by SolarWinds rather than simply identifying them. Step 3 Receive incident determination from CDA Program Manager.
Does the reported incident meet the criteria for. Incident reporting is the first step in a much longer process. It is best to.
Step 4 Reporting person coordinates with. The Security Officer for the organization is the individual responsible for this documentation whether in an electronic or written format. SECURITY INCIDENT REPORTING PROCEDURES ReportallsuspectedorconfirmedSecurityIncidentsImmediately TheUniversityofMassachusettsMedical.
All types of security incidents should be recorded via security incident report form with follow up management involving the investigation risk assessment corrective actions and sign off. In most cases copies of these reports are made available to the client. Reporting Critical Cyber Security Incidents.
-What step is part of reporting of security incidents. Report disclosure to all patients. Security incidents reporting steps.
Exclude notation of incident from the patients medical record. Incident Response Step 2 Response. CFATS Risk-Based Performance Standard RBPS 15-16 Significant Security Incidents.
Asked Aug 30 2017 in Health Professions by Burton_M. What step is part of reporting of security incidents. The focus of this phase is to monitor security events in order to detect alert and report on potential security incidents.
That doesnt mean walking up to face the whistleblower in person and say hey so-an-so I just got your complaint and Im going to look into it. What item is considered part of the contingency plan or business continuity plan. Notify Business Associates and Trading Partners of the breach.
Security incident reporting is a critical component for ensuring all security incidents are captured recorded and managed in the workplace. Building one incident process. IDS Security Services must provide clearance to reconnect or use a system that has been part of an incident investigation and recovery.
RBPS 15 Reporting of Significant Security Incidents and RBPS 16 Significant Security Incidents and Suspicious Activities complement each other and address the importance of developing protocols and procedures for promptly and adequately identifying investigating and reporting all. Report all suspected or confirmed Security Incidents Immediately. While internal reporting of security incidents is an inherent part of security incident policies and procedures the Security Rule generally does not require a covered entity to report incidents to outside entities.
Definitions Information Security Incident. Definition Title II Term What step is part of reporting security incidents. If you see something say something is the motto of the Department of Homeland Security.
Security Incidents Reporting Requirements IF00316. Under contract with CMS conduct audits on highrisk and hospital-specific data from claims data in this report. Having a security incident process in place helps to enforce your companys security policy.
-What step is part of reporting of security incidents. At the conclusion of this Short the student will be able to identify the appropriate reporting requirements to follow in the event of a security incident. Security incident report Contact information.
While these reports can be a source of useful information they should not be considered a substitute for the companys own internal incident reporting system as described above. The security incident report needs to contain certain information to meet compliance. However the real challenges begin once you start looking at why the incident occurred and assess what can be done to prevent these incidents in the future.
This Short identifies the appropriate reporting requirements to follow in the event of a security incident. Activate a Computer Security Incident Response Team CIRT to investigate assess the damage collect evidence report the incident and perform recovery procedures. This helps to limit damage the quicker the.
AReport disclosure to all patients. Its a motto that is also highly relevant to ensuring that our systems and data are secure. The upcoming General Data Protection Regulation GDPR requires your company to notify supervisory authority within 72 hours in case of a.
Therefore incident management procedures should include initial discovery and reporting of suspected incidents or events as the first step. Information security incident refers to an adverse event in an information system network andor workstation or the threat of the occurrence of such an event. In fact reporting of incidents becomes a highly critical aspect of security and business these days.
Change passwords to protect from further invasion. What step is part of reporting of security incidents. Reporting is usually thought of as what happens after an accident dangerous condition injury or near-miss has taken place.
However 164314 a 2 i C and b 2 iv require contracts between a covered entity and a business associate and plan documents of a group health plan. BExclude notation of incident from the patients medical record. Users reporting a security incident will be informed of the resolution or outcome of the incident response and recovery after all investigations have been completed.
CNotify Business Associates and Trading Partners of the breach. An incident reporting system should be configurable to allow escalation through reporting to triage to mitigation whilst ensuring the most appropriate person is alerted once the process of security incident reporting begins. When security incidents occur documentation is required for compliance.
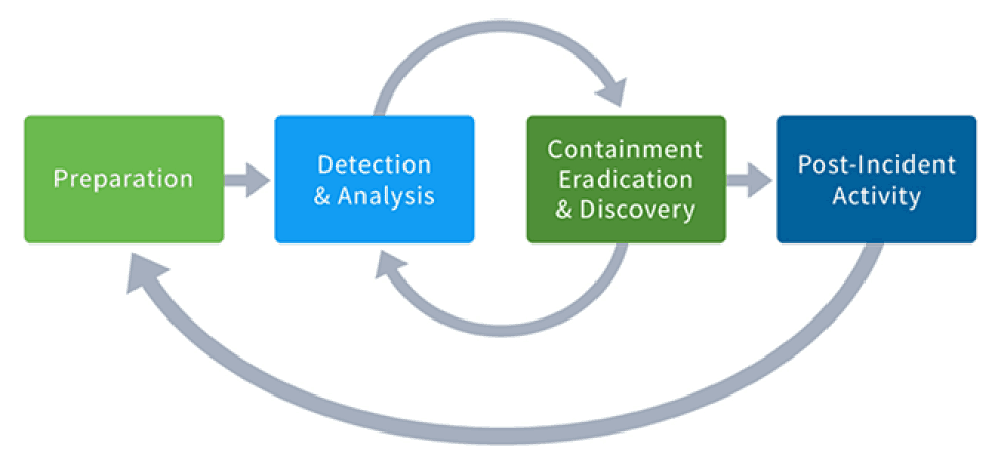
6 Incident Response Steps To Take After A Security Event
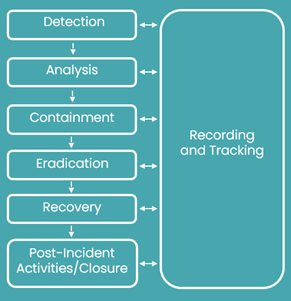
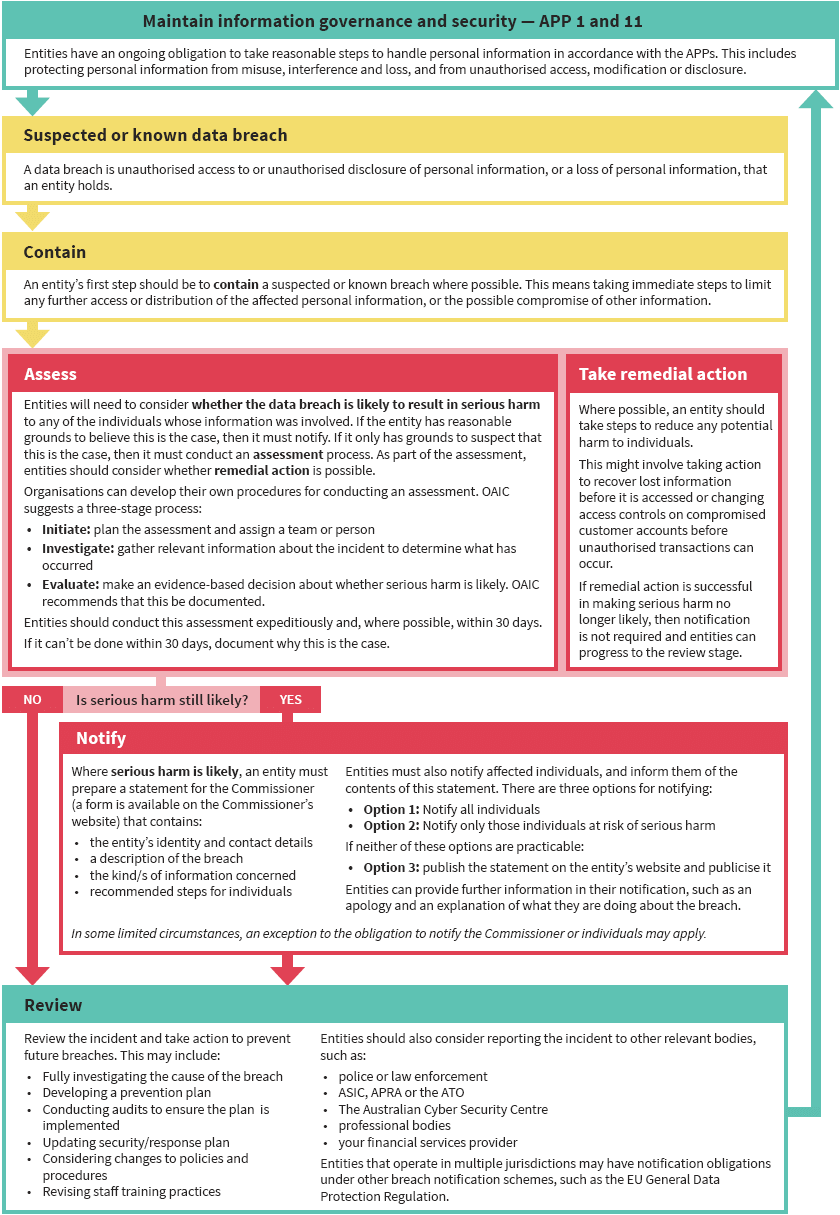
No comments for "What Step Is Part of Reporting of Security Incidents"
Post a Comment